Social Media Technology Connects the Contact Center

For those of us who like welldefined boundaries, social media is problematic.
As individuals, we may prefer to keep our Facebook friends separate from LinkedIn connections, but folks tend to cross-pollinate. As contact center professionals, we may prefer people use traditional forms of contact to request assistance, discuss issues and air grievances, but customers may choose to express themselves in public forums. And if marketing or public relations rule the social media roost, the company may not leverage all the available technology and associated processes to engage the contact center consistently when its skills and expertise are needed.
Although much has been written about social media and its applicability to the contact center, a lot of folks have opted to—or have been forced to—sit on the sidelines. It’s time to get in the game! Unlike other channels, we don’t get to decide whether customers use these channels to communicate with (or about) the company. They make that choice. It’s up to us to join with our colleagues across the company to craft an appropriate strategy for response and avail ourselves of the right tools and processes to implement it.
Are Customers Trying to Make Contact?
Facebook pages, Twitter accounts and corporate LinkedIn profiles have become nearly as commonplace as websites. They’re standard elements of the corporate brand and a ready means for self-promotion. While clever social media administrators find ways to engage the audience and expand the fan base, many check in only to post their latest news and product/service specials.
Unfortunately, customers don’t confine themselves to corporate social media pages when logging their opinions, experiences and complaints. Their commentary populates thousands upon thousands of blogs, forums, consumer review sites, YouTube channels, social networking pages and other Internet-accessible media. Many enjoy the give-and-take of group sourcing to provide answers to questions and/or guidance on purchase decisions. Others need an outlet for frustration when they’ve had a bad experience or have failed to gain a company’s attention through other means.
A telling study by Maritz Research and evolve24 revealed that 49% of Twitter complainants expected companies to read their tweets; only a third of them received responses (http:// bit.ly/uS4UYj) Of those for whom there was no follow-up, 86% would have liked (or loved) hearing from the company regarding their grievances. Companies serving the two-thirds majority missed the opportunity to resolve open issues, bolster relationships with customers, and clean up their soiled reputations. Had they leveraged trained agents in the contact center, they could have queued, processed, resolved and reported on all of these contacts.
Social Media Tools
Although there can be a fair amount of crossfunctional planning and negotiation to navigate the territorial waters for social media, a base knowledge of the available technology to manage this contact stream can facilitate discussion. This technology serves three primary functions: social media monitoring, social media routing, and social customer relationship management (SCRM). search millions of public websites—e.g., online news publications, blogs, forums, photo/video sharing, social networks—to find and extract content based on mentions of defined keywords (e.g., company names, product names, industry terminology). Their analytics engines process all of this data to identify:
- The most important channels and influencers based on vote count, comment count, followers/friends, hyperlinks, views expressed
- Public sentiment about products and services—positive, negative, neutral—based on standard system algorithms and/or customer-defined criteria
- Attitudes toward your company’s and your competitor’s products and services
- Topics and issues around which most comments focus (problem, service request, sales opportunity)
- Individual posts that merit a direct and personalized response based on strong positive/negative comments
These tools can be free, subscription-based, fixed cost, premise-based or hosted. Most provide dashboards and key metrics reporting, and analytical strengths can be a differentiator. The more sophisticated capabilities and support provisions are associated with more expensive offerings. This feature set tends to be associated with departments charged with protecting the company’s reputation and brand image (i.e., marketing, public relations).
Social media routing tools queue actionable mentions from social media monitoring tools to the most skilled and available agent. This functionality has been integrated into most traditional contact center routing solutions. Some have developed their own monitoring solutions to front-end their routing application. Most integrate with third-party monitoring tools. Key features of the routing solution include:
- Ability to identify actionable categories (sales, customer service, marketing, tech support) and assign posts to the appropriately skilled agents
- Integration with other media (voice, email, webchat) for routing to agents who support multiple media streams
- Media translation (e.g., tweet to email, post to webchat, tweet to mobile SMS)
- Contact history, including the last X tweets or posts
Social CRM (SCRM) tools integrate all modes of contact into a coherent, single-view agent desktop application that truly reflects relationships. Through SCRM, agents have access to a complete history of all forms of interaction with each customer. Other key features include:
- Customer record “pop”
- Automatic creation of the customer “case”
- Customer’s social media value (number of followers, frequency of social contributions, etc.)
- Integrated access to agent support resources—e.g., knowledge management (KM) system, searchable library of relevant articles, suggested responses
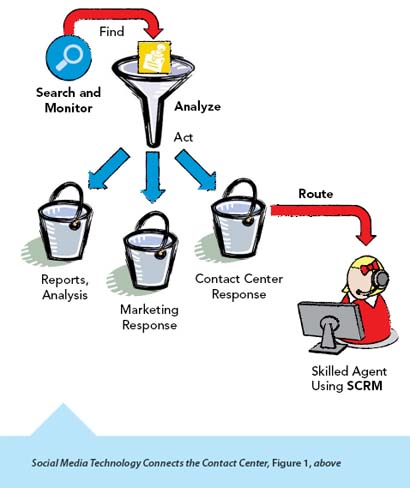 Figure 1 illustrates how the three social media “tools” function in an integrated social media management infrastructure. The monitoring and analysis tool searches the public domain for the designated keywords and parses them into three buckets: (i) include in summary data and analysis only; (ii) send to marketing/public relations for further assessment and action (e.g., respond to competitive announcement, reflect on product positioning, perform damage control on tarnished image); and, (iii) forward to the contact center for personalized customer service. Once forwarded to the contact center, the routing and reporting engine provides the same professional contact management treatment that is accorded to all other media. The SCRM tool supports effective contact handling at the agent desktop and the associated tracking and interaction response. Each of these three elements includes reporting pertinent to its primary role
Figure 1 illustrates how the three social media “tools” function in an integrated social media management infrastructure. The monitoring and analysis tool searches the public domain for the designated keywords and parses them into three buckets: (i) include in summary data and analysis only; (ii) send to marketing/public relations for further assessment and action (e.g., respond to competitive announcement, reflect on product positioning, perform damage control on tarnished image); and, (iii) forward to the contact center for personalized customer service. Once forwarded to the contact center, the routing and reporting engine provides the same professional contact management treatment that is accorded to all other media. The SCRM tool supports effective contact handling at the agent desktop and the associated tracking and interaction response. Each of these three elements includes reporting pertinent to its primary role
One trick to the pursuit of the right technology is that the boundaries that separate the vendors and their solutions are somewhat fuzzy. Most vendors have a “strong suit” and support limited functionality in the other areas and/or bolster their offerings by integrating with (or acquiring) other solutions. For example, many social media monitoring tools have a limited email route capability for attention-grabbing posts, but they lack the ability to apply the full-range of contactprocessing capabilities that are indigenous to multimedia contact routing solutions. Likewise, the contact history feature in a routing solution cannot compare to the breadth and depth of information and functionality inherent in a fullyfeatured SCRM solution.
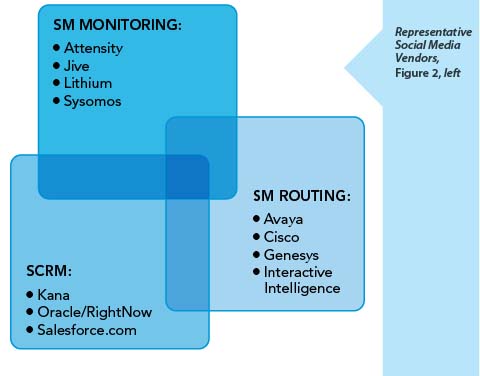
Given that framework for understanding solutions providers, Figure 2, on page 34, shows how leading solutions providers fit within the social media contact management arena.
Social Media Strategy
The traditional planning model places strategy as the launching pad from which all operational and technology decisions flow. To that end, you would crystallize your corporate strategy and consider where and how social networking plays a role in it. You would assess overarching trends for social media, examine your customers’ needs and expectations for this channel, check out your competitors’ strategies and tactics, and get a sense for the cost structures associated with different support options, both operationally and technologically. And you’d equip yourself with “best practices” to do the job well.
 The traditional planning model doesn’t always happen in practice, and certainly not with respect to a channel characterized by rapid change, a relative lack of control by its corporate participants, and the broad spectrum of opinions surrounding its strategic importance. Strategy may evolve from a more organic place in which there is exploration, discussion, experimentation and refinement. And strategic planning can be informed by reviewing the tools you have in place and the opportunities to extend them further into more cohesive channel management.
The traditional planning model doesn’t always happen in practice, and certainly not with respect to a channel characterized by rapid change, a relative lack of control by its corporate participants, and the broad spectrum of opinions surrounding its strategic importance. Strategy may evolve from a more organic place in which there is exploration, discussion, experimentation and refinement. And strategic planning can be informed by reviewing the tools you have in place and the opportunities to extend them further into more cohesive channel management.
To that end, do some initial reconnaissance work to make sure that you have a sense for what the social media monitoring, routing and CRM can do for you. Take inventory of what you already have in the contact center, and what can be readily added to your existing investment. Armed with that information, you’re ready for an engaging conversation with your organization’s social media gurus.
Entertain a roundtable discussion with the folks who manage your organization’s social media channels. Find out where and how they currently engage with your constituencies—on venues managed by your company (e.g., your corporate Facebook page) as well as third-party sites. Ask for a tour of their social media monitoring tool and how it’s used today. (If they don’t have one, you’ll have an opening to talk about what’s out there and why they should consider using one!) Focus on circumstances in which individual posts may translate into a need for personalized attention and response. Find out how those interactions are addressed today.
Now it’s time for you to educate your counterparts on what’s possible in the contact center domain. Give them an overview of your core competencies with respect to contact management—queuing, routing to appropriately skilled agent, integrated contact management tools at the agent desktop, and reporting. Highlight the benefits of leveraging the contact center as the means to address real-time interaction with customers on information and service requests. Let them know what kind of information and insights you’re capable of sharing with them. Talk about options for integrating your routing capabilities with social media monitoring, and how the tools fit within an integrated social media contact management framework. And assure them that through knowledge management and the routing and SCRM tools, they can play a role in helping to define the library of common responses and track, review and optimize the messages being delivered through timely interaction handling.
Having traversed the educational gap, you and your colleagues can roll up your sleeves and take a good look at the broad spectrum of social media posts with which your company has an interest and discern which ones reasonably “belong” to which department. You can discuss the criteria by which you’d make that determination and how they could be instituted within your existing (or needed) tools. You could develop processes for handling contacts, providing “hand-offs” when contacts are best addressed by other departments, and sharing information and insights. And you can invite marketing to collaborate on agent training to ensure proper social media complaint resolution, escalation, brand protection and promotional messaging for upcoming marketing campaigns or other activities. The tools, along with the collaboration, ensure execution of consistent and clear “rules of engagement” with customers under various circumstances.
With an actionable strategy that incorporates feature-rich technology with the proper assignment of cross-department functionality, your organization will be properly positioned to effectively handle this customer contact channel.